Is Empower affected by the planned Microsoft hardening changes to DCOM security described in KB5004442 (CVE-2021-26414)? - WKB230033
ENVIRONMENT
- Empower
- Microsoft KB5004442 (CVE-2021-26414)
ANSWER
It is important that the DCOM hardening changes described in Microsoft article KB5004442 are applied to all Empower nodes.
Empower does not implement a specific DCOM security level in the code. Empower is designed to use the default level specified at the Operation System (OS) level.
Waters testing has shown that if the DCOM hardening changes described in the Microsoft article KB5004442 are not applied to all Empower nodes there are potential impacts to Empower function. Areas of concern include accessing node and system properties, use of ACQUITY Console, initiating acquisition, data transfer from LAC/E to Raw Data Server, and remote data processing (SQT, Run and Process, Run and Report). These effects are expected to be exhibited when using or accessing Empower nodes that have not had the changes applied.
Waters will continue to update this article as new information is learned.
ADDITIONAL INFORMATION
Please note KB5004442 is not the specific patch that implements this change. Customers are advised to review the information detailed in Microsoft Article KB5004442 to understand the planned timing for the change and possible remediation steps until the change becomes permanent.
One of the most practical ways to determine if the particular Windows installation is patched to a level where the DCOM hardening changes are enforced is to execute WINVER via the Start Menu or Command Prompt window. The output of WINVER will display the OS Build. e.g. 19044.3324.

Using this information, one can determine the date the build version was released. e.g.
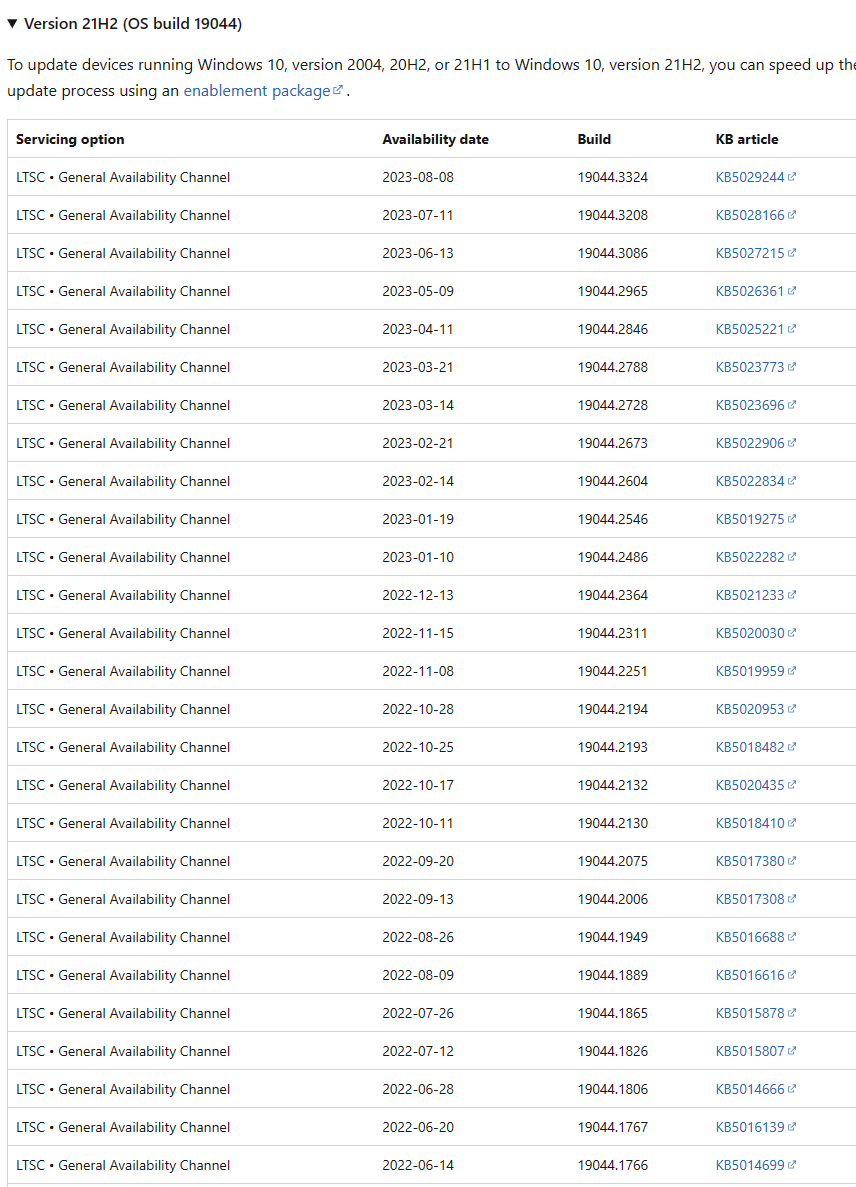
To ensure the OS is accommodating the DCOM hardening changes, the OS should be patched to a Build Version released in June 2022 or later.
id230033, EMP2LIC, EMP2OPT, EMP2SW, EMP3GC, EMP3LIC, EMP3OPT, EMP3SW, EMPGC, EMPGPC, EMPLIC, EMPOWER2, EMPOWER3, EMPSW, SUP

